The world’s largest ticket retailer is in hot water after their parent company, Live Nation Entertainment filed an 8-K filing with the Security and Exchange commission admitting that they had been hacked to the tune of 1.3 terabytes of information. That amounts to 560 million customers’ personal information that has been stolen from the company’s servers. Today, we take a look at the hack and what it means for consumers.
Hackers and cybercriminals, like most people, tend to gravitate towards high-reward activities. In this case, that means that focus is turning to creating malware that attacks the router, potentially infecting the users that leverage it to connect wirelessly to the Internet. Researchers at Kaspersky Lab recently discovered an example of such a malware, so today, we will review this threat and how to best protect your network.
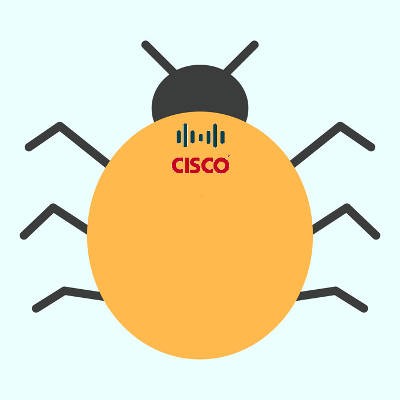
Virtual private networks are vulnerable to an exploit that was recently brought to light. Cisco has announced that this exploit undermines its ASA, or Adaptive Security Appliance tool. If this issue isn’t patched immediately, you could find your organization vulnerable through remote code exploitation.
In a statement given by Tom Bossert, the homeland security adviser to the White House, blame for the WannaCry attacks leveraged from May 12th to the 15th in 2017 was attributed to the Democratic People’s Republic of Korea. This assertion is in line with the conclusions that New Zealand, Australia, Canada, and Japan have come to, according to Bossert.
Using the most up-to-date versions of your technology’s operating systems is one of the best ways to stay secure. Yet, some organizations forego the jump to more recent operating systems due to the immense up-front expense represented by upgrading multiple servers or workstations at once. Unfortunately, this can be detrimental to your organization’s security, and potentially even put your business’s future at risk.
ATMs are, surprisingly enough, not the most secure pieces of technology out there, though there are efforts to improve security by taking advantage of mobile devices. Granted, this won’t be enough to protect against the considerable vulnerabilities in ATMs. In order to maximize security and minimize the amount of damage done by vulnerabilities, the user needs to understand how to protect themselves while using ATMs.
If we told you that automated teller machines, or ATMs, were susceptible to hacking attacks, would you believe us? You should; there are a plethora of ways for hackers to infiltrate and steal money from ATMs, with the latest being so dangerous that even the Secret Service has issued warnings about it.
Every security professional’s worst nightmare consists of the National Security Agency (NSA) being hacked. While there’s no proof that the NSA itself has been hacked, there is some evidence to suggest that some of the exploits used by the agency are up for grabs on the black market. What this means is that a lucky group of hackers could potentially get their hands on some very dangerous tools.
The Internal Revenue Service is one organization that you don’t want to mess with. Thanks to their antics filing fraudulent tax returns through the often-exploited Get Transcript site managed by the IRS, Anthony and Sonia Alika have to do some time in the slammer; and that’s not even mentioning what they have to pay the IRS in restitution.
Ransomware, the malware variant that has appeared more and more frequently has struck again, this time targeting users of Microsoft Outlook in a zero-day attack. A malware variant of Cerber (a ransomware) was recently utilized in a large scale attack on users of the messaging program, sent via phishing emails to corporate users.
27 vulnerabilities: The amount of vulnerabilities that were resolved with the round of security patches in Microsoft’s latest Patch Tuesday. Windows, Microsoft Office, Internet Explorer, the Edge browser, and more, were all affected. It’s important to patch these vulnerabilities as soon as possible, especially if you haven’t done so already.
The Petya ransomware, a particularly vicious monster of a threat, has reared its ugly head once again, only this time, it’s not alone. Petya now comes bundled together with Mischa, yet another ransomware that works well alongside Petya. The ransomware is delivered via an inconspicuous email disguised as a job application, with a resume attached. Once the user downloads the file, Petya encrypts the files located on the device.
While security experts tend to focus the brunt of their discussions on desktop OS vulnerabilities, there are plenty of mobile malware threats that fly under the radar. One such malware is called Hummer; a trojan that installs unwanted apps and malware on a device, and can be found on over a million phones worldwide.