Small businesses today generate a lot of data. From customer details and sales records to inventory tracking and employee schedules, you need to be able to structure this data so that you can use it effectively. Keeping that data organized and accessible is important, but managing it effectively can often be a hassle. This is where smart database management comes in. When done right, it helps businesses run smoother and often save money.
If you or your business are worried about cybersecurity, we’d like to say, “Congratulations, you get it!” Too many people fail to take cybersecurity seriously, and with hackers and data breaches making headlines worldwide, you cannot underestimate them. Today, we want to cover how a cybersecurity consultant can save you time, money, and stress over your security systems.
There are many parts of running a business where you cannot be too careful, one of which is the realm of cybersecurity. Many of the preventative measures you can implement aim to keep issues from making their way to your infrastructure in the first place, which makes sense from an operational standpoint. With an endpoint detection and response solution—or EDR—you’ll take an important step toward keeping most threats off your infrastructure.
Your typical IT professional might suggest some common methods of network security like implementing better preventative measures, like firewalls and antivirus. However, there is more that goes into network security—far more. If you’re not careful, you could accidentally miss some of these three security solutions and expose your business to potential threats. But we’re not about to let that happen!
If you are old enough to remember when antivirus (like most computer software) came in a great big textbook-sized box at the store, then you probably remember a time when that was the only protection you really needed.
Today, there are countless free versions of antivirus out there. Let’s talk about how much protection these actually bring, and when and where they might be a good fit.
You don’t need us to tell you that ransomware is a problem (or maybe you do–we mean, it’s a huge problem). It’s dangerous to both businesses and individuals, and it has become such a common threat that all organizations need to have a plan in place to address it with their staff. Today, we want to highlight a three-part strategy that you can use to approach ransomware in the most secure way possible.
The IoT, or Internet of Things, is everywhere. There’s a relatively good chance that a device that would be part of the IoT is within your reach right now, perhaps even on your person. Businesses of all kinds use the IoT for various purposes as well, but behind this usage lies significant risk from cyberthreats, and a shocking number of businesses seem to accept this risk without much concern… as in, the vast majority of surveyed businesses utilizing the IoT demonstrated a lack of protection, but seemed not to be bothered by it.
AI—artificial intelligence—has been a hot topic as of late, with it seemingly being used for any purpose you can imagine nowadays. Unfortunately, this has also included cybercrime.
However, just as AI can be a weapon for cybercriminals to use, it can also be a shield to help protect your business from threats. For instance, in phishing prevention.
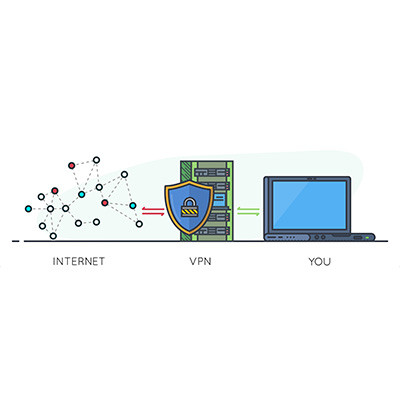
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses use a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Let’s go over why a VPN is so effective, as well as what you should look for in a business-grade VPN tool.
Wi-Fi connectivity is a remarkable technology when you really think about it, and it has fundamentally changed how we work today. What hasn’t changed, unfortunately, is that hackers and cybercriminals will try to use this technology to their own advantage. Therefore, let’s discuss a few relatively simple ways that you can improve your wireless network’s overall security.
The modern threat landscape is vast and unpredictable, and even if you think you know enough about cybersecurity to protect your business, we bet that you don’t. It’s not even just in the business world, either; individuals also struggle against cyberthreats, and so too do IT administrators. The next couple of weeks will be dedicated to cybersecurity to get across everything you need to know about it.
Whether you love them or hate them, passwords serve an important purpose in the realm of cybersecurity. They are the first line of defense against potential threats, yet they are also notoriously easy to crack. Some of the biggest names in technology have been working on ways to get around the challenges presented by password security, including one that we are excited to highlight in today’s blog.
It hasn’t been very long since T-Mobile experienced its latest major hack, but unfortunately, here we are again. Hackers have again accessed customer data, with 37 million customers being affected amongst both their prepaid and subscription-based accounts.
Let’s dive into the situation, and what can be learned from it.
For a long time, businesses that didn’t have any cybersecurity problems would never consider investing in additional cybersecurity tools. The decision-makers of these companies simply didn’t find it necessary; and many of them had a point (until they didn’t). Today’s threat landscape is much, much more complex than it was only a few short years ago and therefore businesses need to make a point to set up the security tools that will help them secure their network and infrastructure from threats. Let’s take a look at some strategies that work to help modern businesses secure their digital resources:
If Edgar Allan Poe worked in an office, here’s what one of his works would sound like:
True!—nervous—very, very dreadfully nervous I have been and am, but why will you say that I am mad? The office had sharpened my senses—not destroyed—not dulled them. Above all was my sense of hearing. I heard all things in heaven and on earth and many things in…the other place. So, how then am I mad, especially when I can so healthily and calmly tell you this story?
When it comes to your business’ cybersecurity, it can be too tempting to operate under the assumption that the few cybersecurity events you hear about on the news are all that happen. Unfortunately, this is far from actual fact. Let’s review some of the statistics that might change your impressions, especially if you hold the aforementioned assumption.
As Miguel de Cervantes wrote in Don Quixote, “...is the part of a wise man to keep himself today for tomorrow, and not venture all his eggs in one basket.” It was wise advice then, and it’s wise advice now—especially when it comes to your business’ network and your data security.
Let’s explore the concept of network segmentation, and how it can help to protect your business.
We are major advocates for multi-factor authentication, but it’s also important to understand that it’s not a catch-all solution. In fact, it has forced cybercriminals to be even more innovative to find alternative methods of attack. One method hackers use to gain access to your systems is to use what’s called MFA fatigue to their advantage.
Let me ask you a few questions—first, how confident are you that you could spot an online ruse, and second, did you know there’s a stain on your shirt right now?
Did you look?
If so, you’ve just fallen for the school playground version of social engineering, a serious threat. Let’s discuss the kind that you’re more likely to see in terms of your business’ cybersecurity.